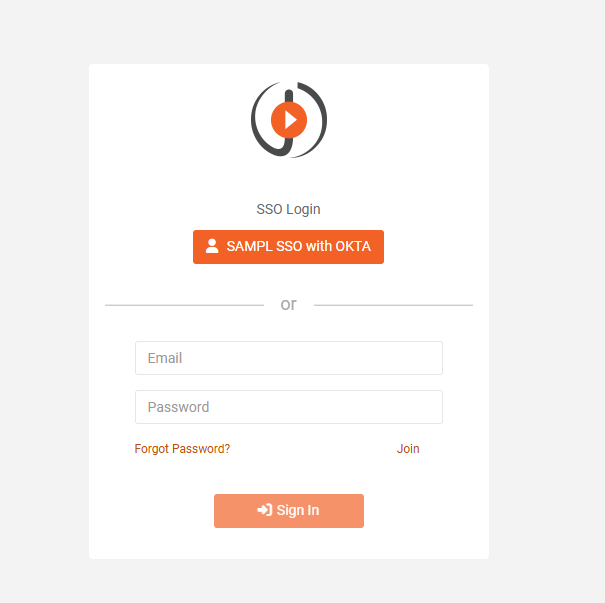
How to Setup SAML-P SSO using Okta
SAML allows its users to seamlessly access multiple applications with their same credentials offering them faster and efficient business conduct. VIDIZMO provides SSO functionality to all of its customers with SAML making it easier to login without having to type in different credentials every time. For more information about VIDIZMO SSO Apps, read Understanding Single Sign-On.
Before you start
- Ensure that you belong to a group where the Management of SSO + SCIM permission is enabled to access this feature to configure SAML-P SSO using Okta.
- For configuring Okta SSO with SAML, you must have an Okta developer account so that you can create an Okta application. For creating an Okta account, visit.
- If more SSO Apps have been configured and enabled on your Portal other than your users will see multiple buttons on the login page allowing them to choose any identity provider of their choice to log in to their VIDIZMO Portal.
- VIDIZMO requires your Okta authorization server to expose a list of scopes to map attributes and provide user authentication. These scopes include:
- Profile (The user's First Name and Last Name are exposed and mapped in your VIDIZMO account in this Scope)
- Email (The user's Email Address is exposed and mapped in your VIDIZMO account in this Scope)
- Groups (This is a custom Scope that must be exposed by your Authorization Server.)
Configuration in Okta
Creating Application
Firstly, you are required to create an application in Okta in order to configure SAML-P SSO using Okta in VIDIZMO. The following steps show you how to create an application in Okta:
1. Go to https://login.okta.com/ and enter the ORG URL that you received while creating your Okta developer account.

2. At the Sign In page:
i. Enter your email address and password.
ii. Click on Sign In.
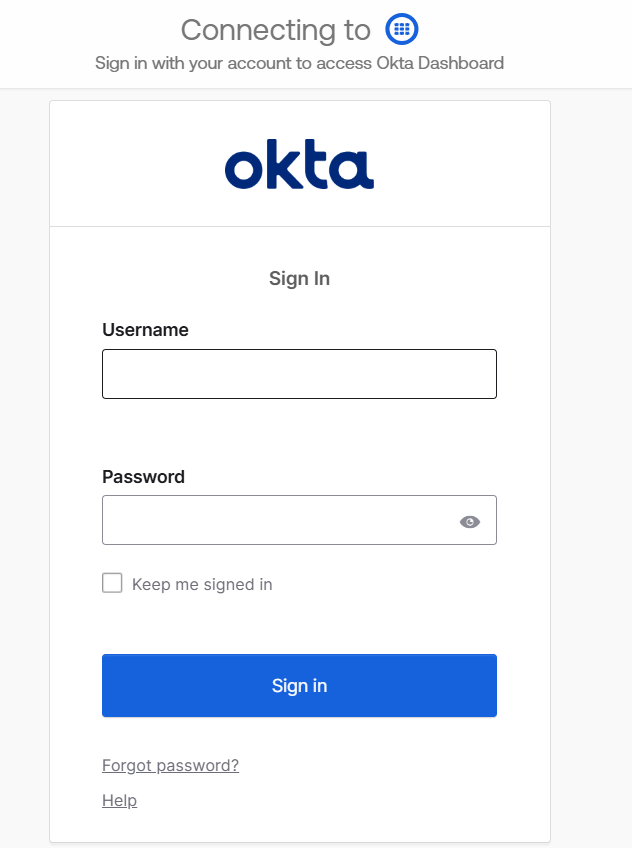
3. From the Developer's Dashboard, click on Applications.
i. Navigate to Applications in Okta Dashboard. ii. Click on Create App Integration
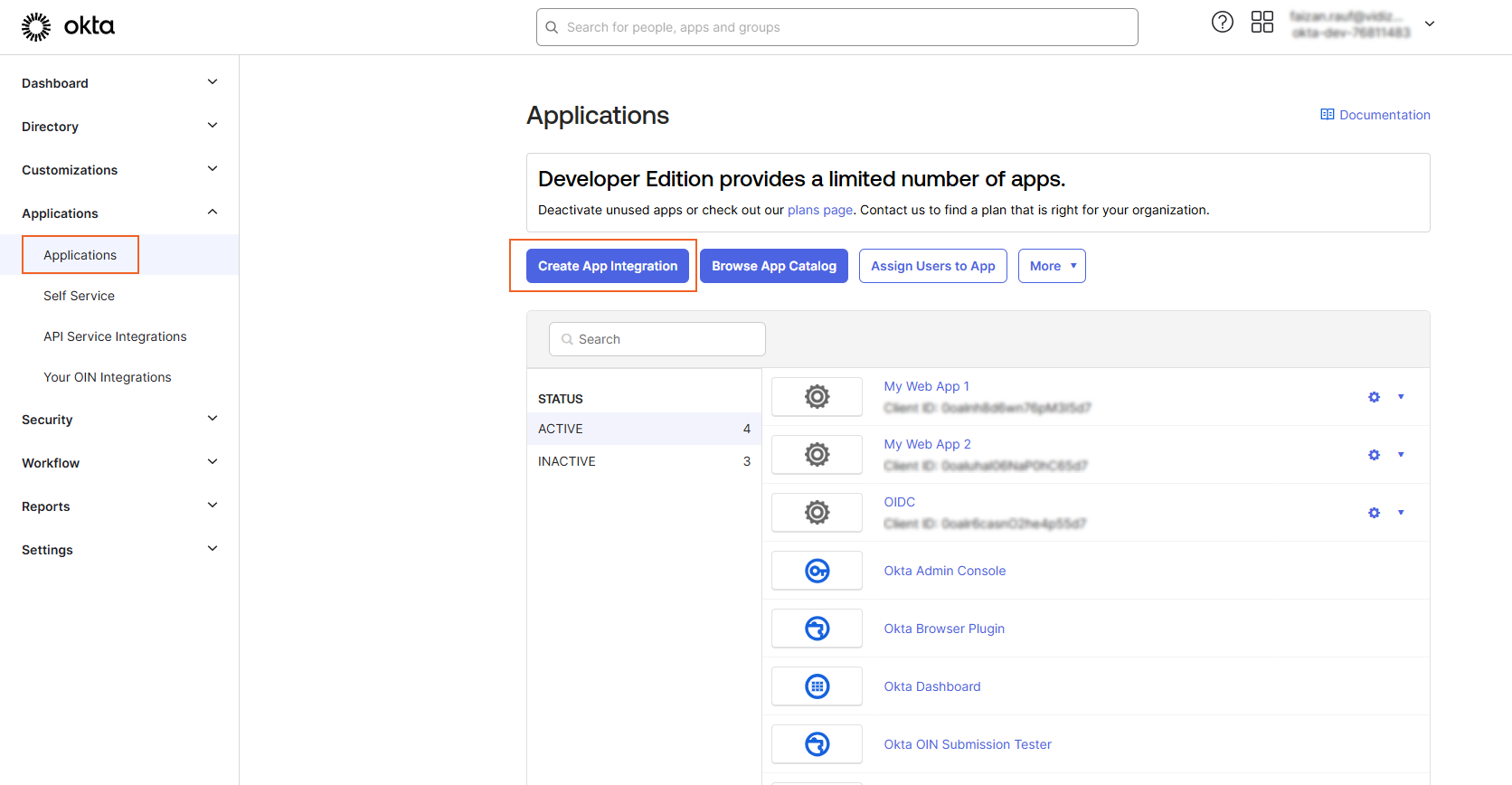
4. From the Create a new app integration page: i. Select the Sign-in Method: Choose SAML 2.0 ii. Click next.
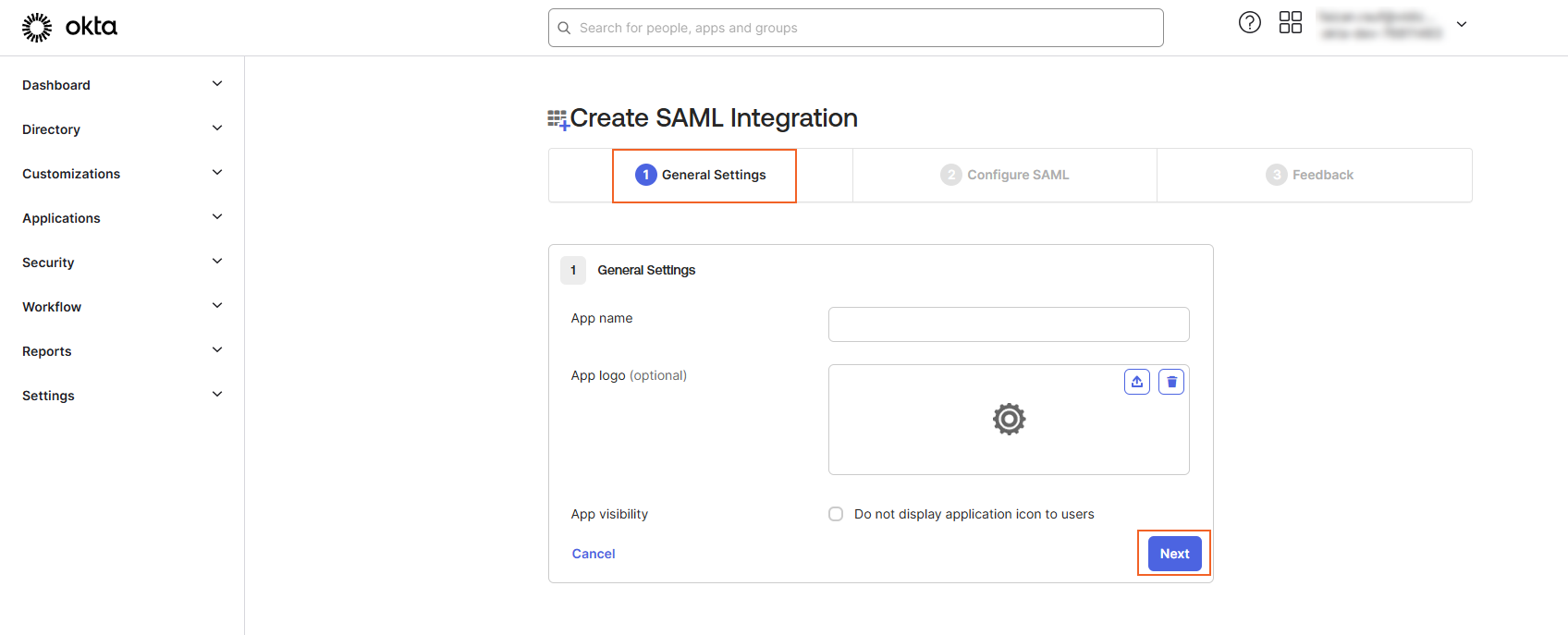
5. On Create SAML Integration App page under General Settings tab.
i. Give your Okta App a suitable name.
ii. Click Next to navigate to the Configuring SAML page.
6. On Configuring SAML tab:
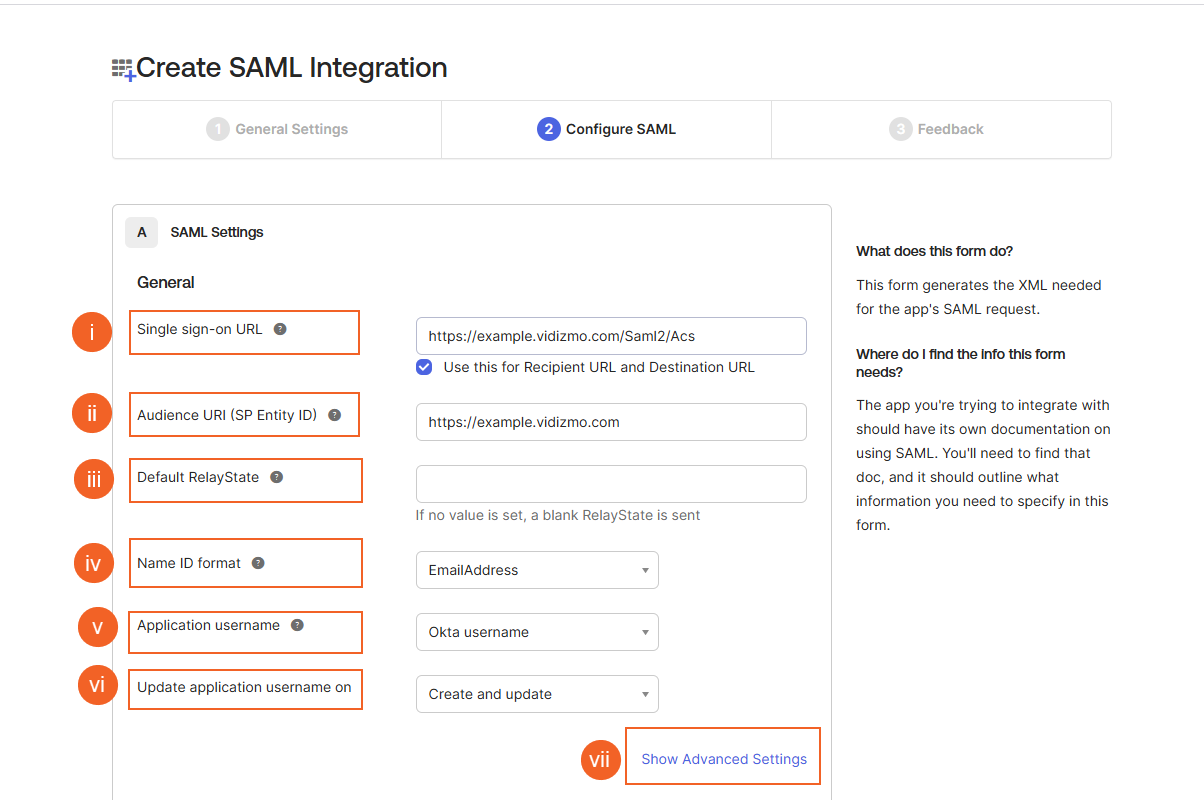
i. Single Sign-on URL: The location where the SAML assertion is sent with an HTTP POST. You need to append /Saml2/Acs in your VIDIZMO Portal Url in order to create this link.
Example: https://example.vidizmo.com/Saml2/Acs
ii. Audience URI: Enter here your VIDIZMO Portal URL. iii. Delay Relay State: Leave this field blank. iv. Name ID format: Identifies the SAML processing rules and constraints for the assertion's subject statement. Use the default value of 'EmailAddress' here. v. Application username: Determines the default value for a user's application username. The application username will be used for the assertion's subject statement. Use the default value of 'Okta username' here. vi. Update application username on: Use the default value of 'Create and update' here. vii. Show Advanced Settings: Click here to see the Advanced Settings.
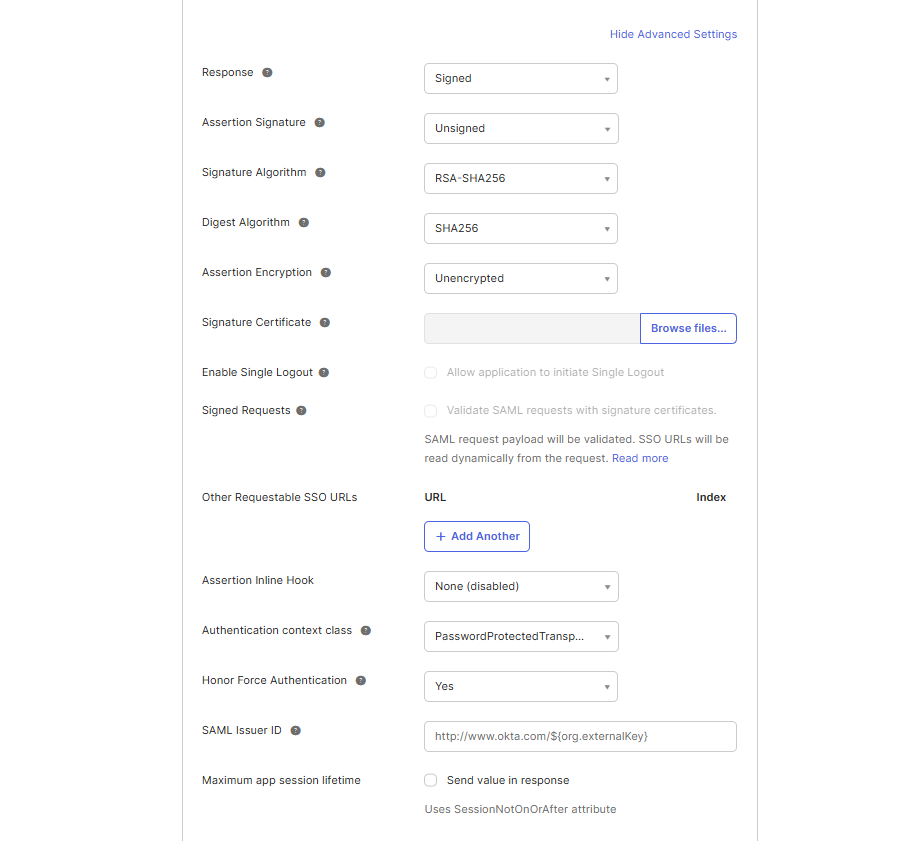
-
Response: Determines whether the SAML authentication response message is digitally signed by the IDP or not. A digital signature is required to ensure that only your IDP generated the response message. Use the default value of 'Signed' here.
-
Assertion Signature: Determines whether the SAML assertion is digitally signed or not. A digital signature is required to ensure that only your IDP generated the assertion. Use the default value of 'Unsigned' here.
-
Signature Algorithm: Determines the signing algorithm used to digitally sign the SAML assertion and response.
-
Digest Algorithm: Determines the digest algorithm used to digitally sign the SAML assertion and response.
-
Assertion Encryption: Determines whether the SAML assertion is encrypted or not. Encryption ensures that nobody but the sender and receiver can understand the assertion. Use the default value of 'Unencrypted' here.
-
Assertion Inline Hook: It would be None (disabled) by default.
-
Authentication context class: Identifies the SAML authentication context class for the assertion's authentication statement. Use the default value of 'PasswordProtectedTransport' here.
-
Honor Force Authentication: Prompt user to re-authenticate if SP asks for it. Use the default value of 'yes' here.
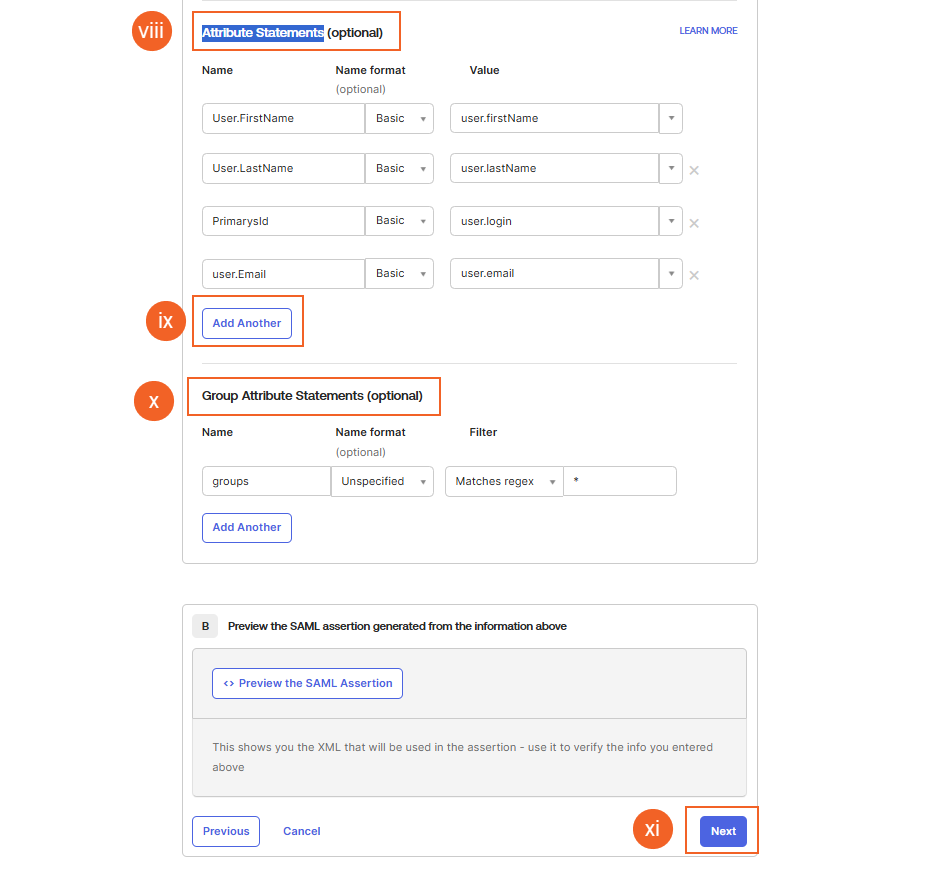
viii. Attribute Statements:
ix. Click Add Another here to add Name format. Add Name formats as shown in the screenshot.
x. Specify the Groups Attribute Statements or Filter, select Matches regex and specify .* as the condition.
xi. Click on Next to move on to the Feedback tab.
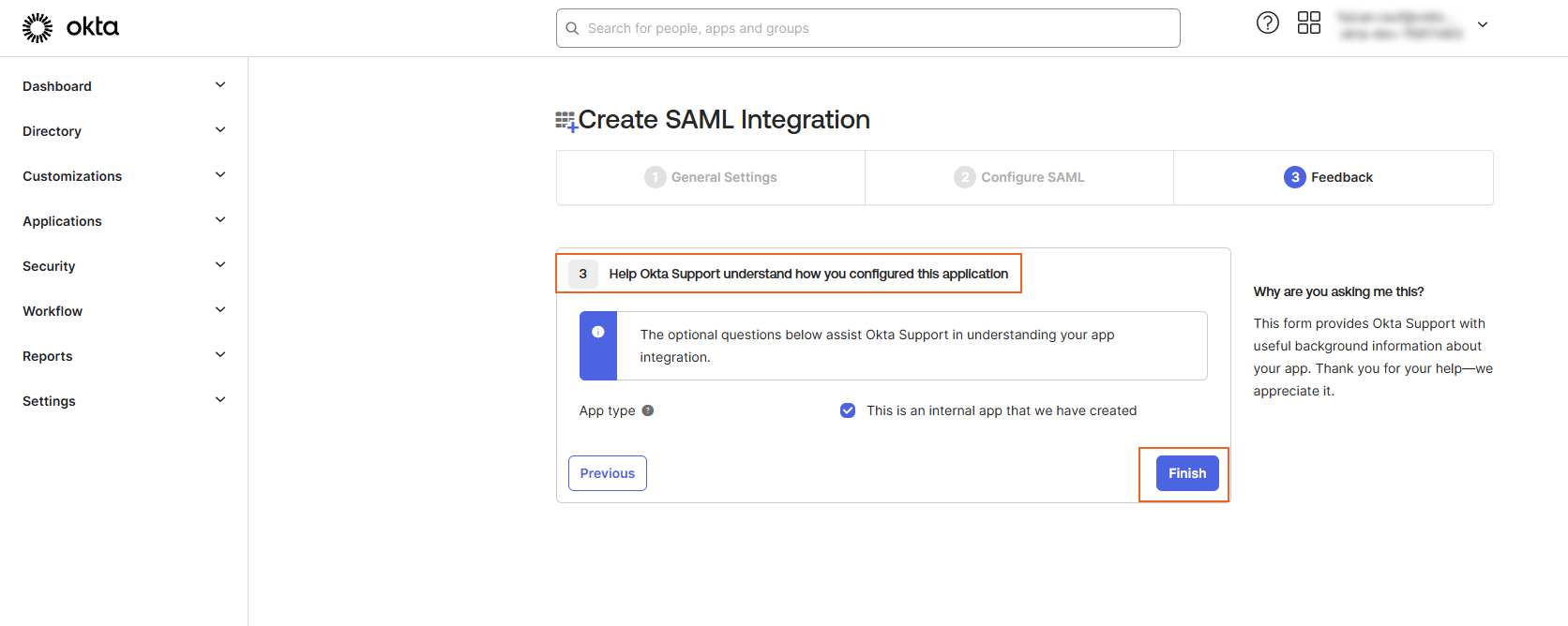
7. From the Feedback tab:
i. (Optional) Select any option.
ii. Click on the Finish button.
8. You will be navigated to your App page from here:
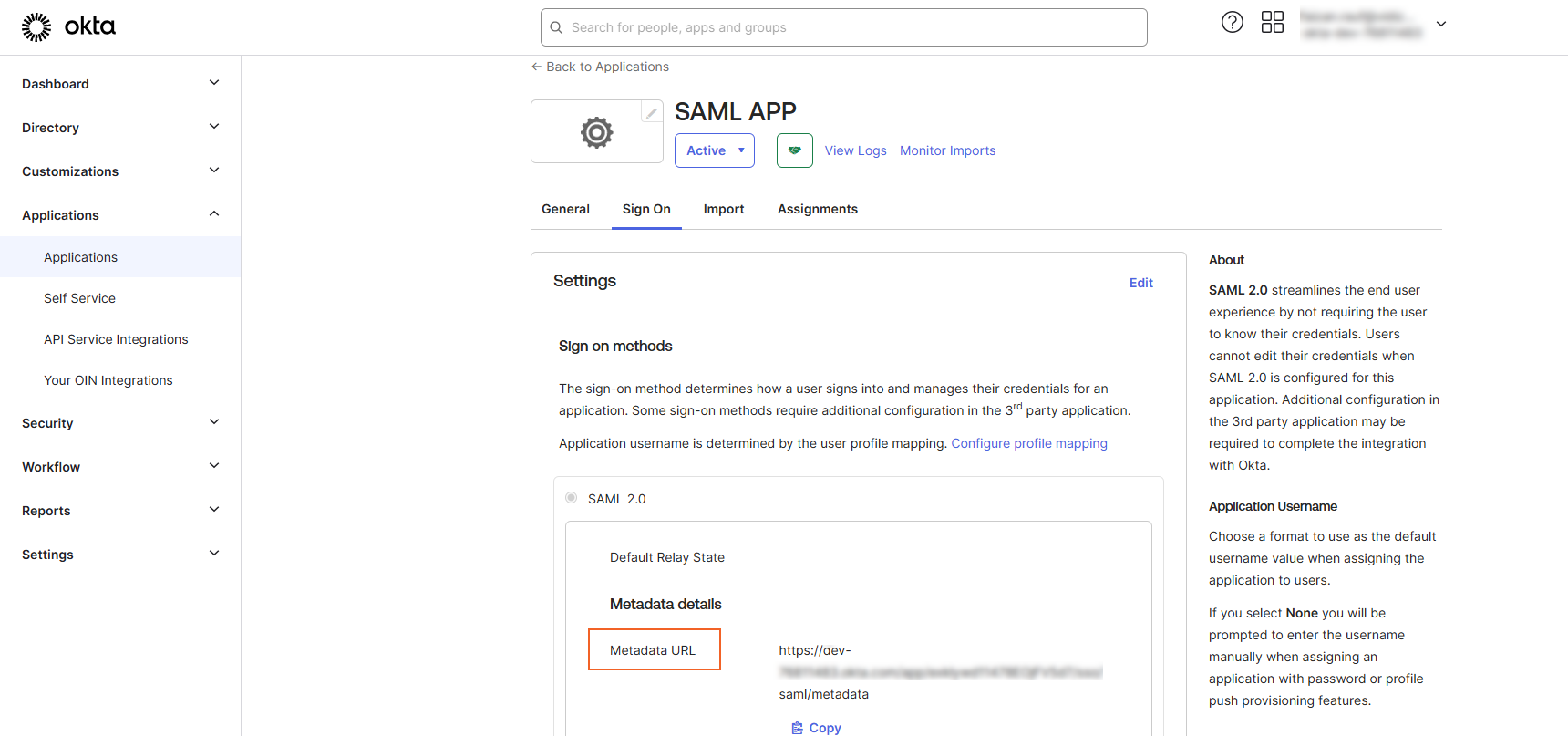
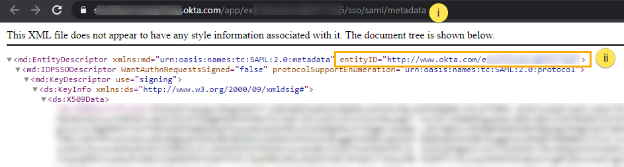
i. Select the Sign On tab. ii. Locate the Metadata URL and copy it. ii. This URL will be used as the Meta Address in the VIDIZMO configuration section. iii. To Retrieve the Entity ID open a web browser and paste the Metadata URL into the address bar of your web browser. iv. Locate the Entity ID in the response, copy it, and save it.This will be used as the SAML Issuer in the VIDIZMO configuration section.
Configuration on VIDIZMO Portal
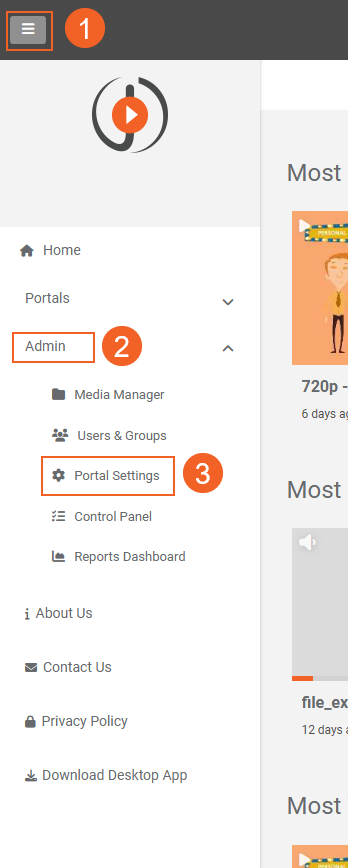
- From the Portal's Homepage click on the navigation menu.
- Expand the Admin tab.
- Click on the Portal Settings tab
- From Portal Settings page, click on the Apps tab.
- Further click on the Single Sign-On tab.
- Locate the SAML at the right-hand side and click on the gear icon to open SAML P SSO - Settings.
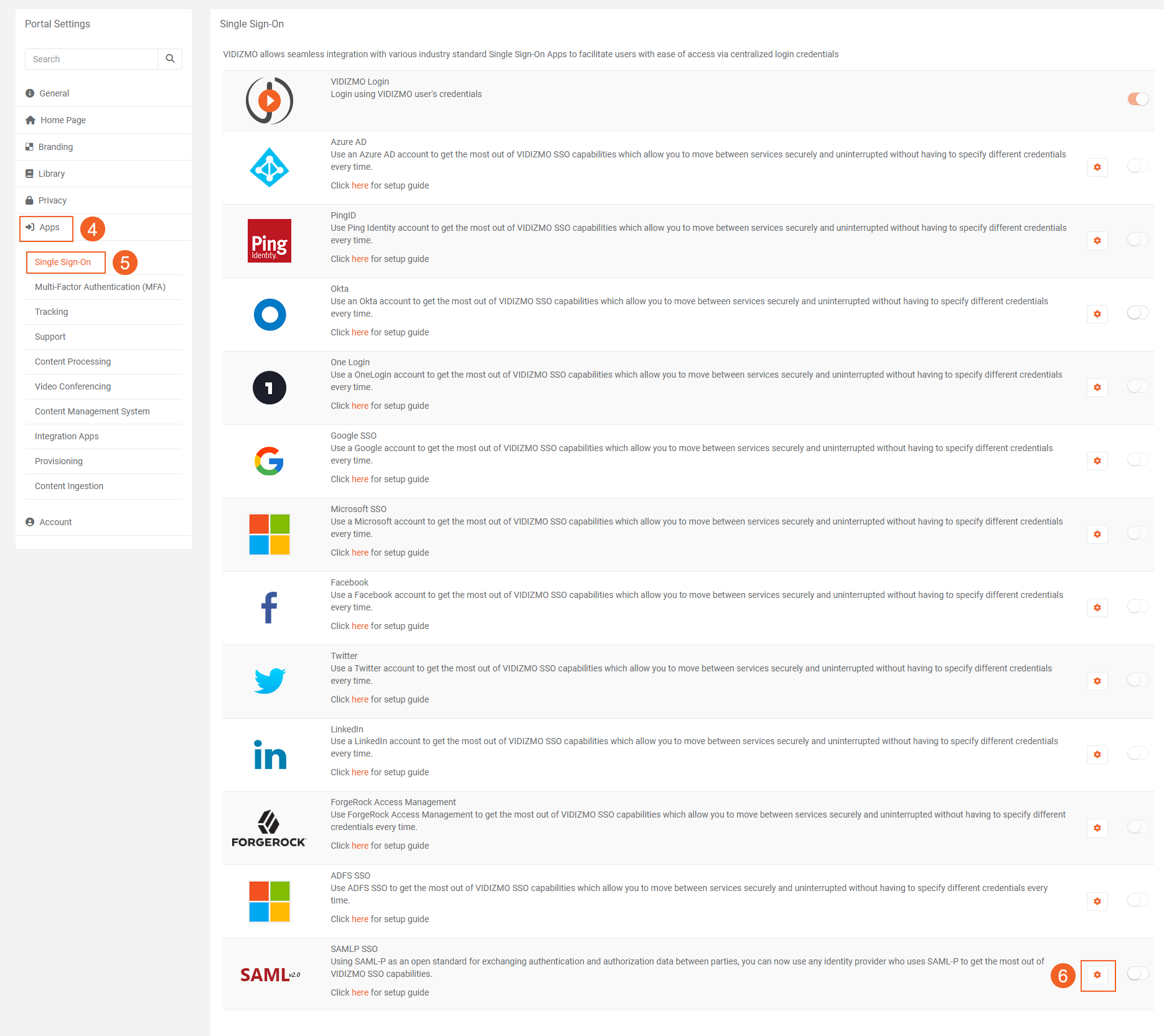
- In the SAML P SSO - Settings screen:
i. Samlp Issuer: Enter the Entity ID copied above.
ii. Meta Address:: Enter here Meta address copied above.
iii. Portal Identity: Your portal URL (e.g. https://lexcorp.enterprisetube.com/)
iv. SSO Login Message: Enter here the message that you want to display on your portal login screen for Okta login.
v. SSO Login Button Label: The text entered here would display on the button used for Okta login.
vi. Callback Path: Specifies the callback location where the authorization will be sent to your Portal.
vii. Force Login: Select the checkbox to enable forced login and it will take you directly to Okta. When unchecked, it will not redirect automatically to the IdP and you will be required to sign in through your Portal's sign-in screen.
viii. Attribute Mapping: Attribute Mapping allows you to map your attributes with the IDP's attributes.
- If multiple CAL (Client Access License) types are available in your VIDIZMO portal, you can select the desired CAL type. This selection will be automatically applied to all users who log in to the VIDIZMO portal using Okta SSO.
- Note that after the automatic sign-in and CAL assignment, the number of available CALs should be dynamically decreased and reflected consistently across all application screens displaying the remaining count, such as on the consumption screens.
ix. Click on the button Save Changes.
A notification will appear stating Portal Information Updated Successfully.
- Enable the toggle button of the SAMLP app.
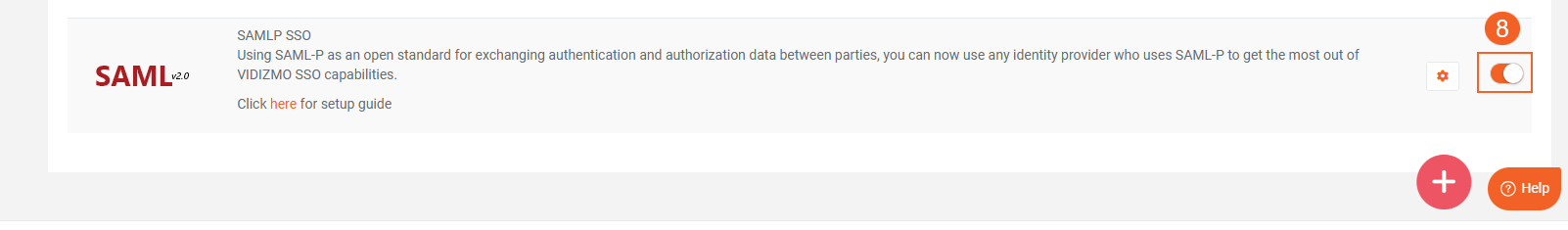
Result
Navigate to the Portal's login screen and you will see an option Login with SAMLP SSO.